Overview of My Theses
Habilitation: Trust & Security in IoT: Monitoring with Constrained Devices
University of Zurich (Switzerland)
Today nearly every device is connected directly or indirectly with the Internet leading to a network of networks building the so called "Internet of Things" (IoT). The devices used show manifold diversity concerning resources, operating systems and communication standards. Usually they are configured to report measurements periodically and for a long period of time resulting in a big amount of data including sensitive information (e.g., GPS, IP addresses, names). These circumstances would not be a problem at all if the IoT would be a trustworthy environment. Looking at the news the reality is different; information becomes public due to hacking or misconfiguration of devices, standards and services used. Especially, the rise of third-party services, which might not be trustworthy but user friendly and the increased awareness of users concerning privacy make the situation even more complex. From the legal point of view, the rights of data owners are now increasingly protected and supported, either by appropriate consumer associations or by the EU General Data Protection Regulation (GDPR). However, users are still not enough informed about what happens with the data gathered as soon as they leave the controlled and owned environment, for example, when using an App of a third-party service provider to visualize their data. Questions concerning data owners are manifold such as "Can I trust the third-party service provider that my data is only used for authorized processing based on signed contract?", "Is my data processed in a secure manner?", and "If data deletion is requested by me, can I be sure that it is really deleted and, thus, forgotten?".
Therefore, this habilitation establishes a common understanding of the IoT, especially about challenges caused by constrained (= lightweighted) devices and concerns raised by users. Further, it presents an overview of communication standards used in the IoT show- ing that the IoT landscape is very complex and no clear layered architecture is identified yet. Thus, this habilitation specifies such an architecture for the IoT by defining clear layers and functional characteristics per layer. With this architecture and knowledge in place, a security analysis of the current situation is performed with special focus on how foreigners can get access to gathered data. Further, tools and techniques (e.g., attacker models, cryptography) are recommended to overcome the existing security problems in general but might not be applicable all the time (e.g., due to too less resources or other obligations of standards or algorithms use). The security issue becomes highly relevant when looking at constrained networks as part of todays IoT. Such constrained devices might become overwhelmed soon when performing complex security because they have limited computational capacity and memory in place. Thus, this habilitation focuses on lightweighted solutions securing communication between constrained devices. Further, due to the increasing mobility of users and the request to access the network and owned data from everywhere in the world, outside services and interfaces need to be integrated in the environment. Such services should regulate the access to the network and its collected data leaving the complete control to the network and data owner in order to integrate a trustworthy service. Therefore, another focus of this habilitation is set on user authentication mechanisms in order to establish a trustworthy outside service fos- tering End-to-End (E2E) security beyond the classic boarders of a constrained network. This means only authorized persons can get access to the network and the network/data owner can grant, update and revoke privileges immediately. In turn this reduces the involvement of a third-party, i.e. administrator, to a minimum and ensures complete control to the network/data owner.
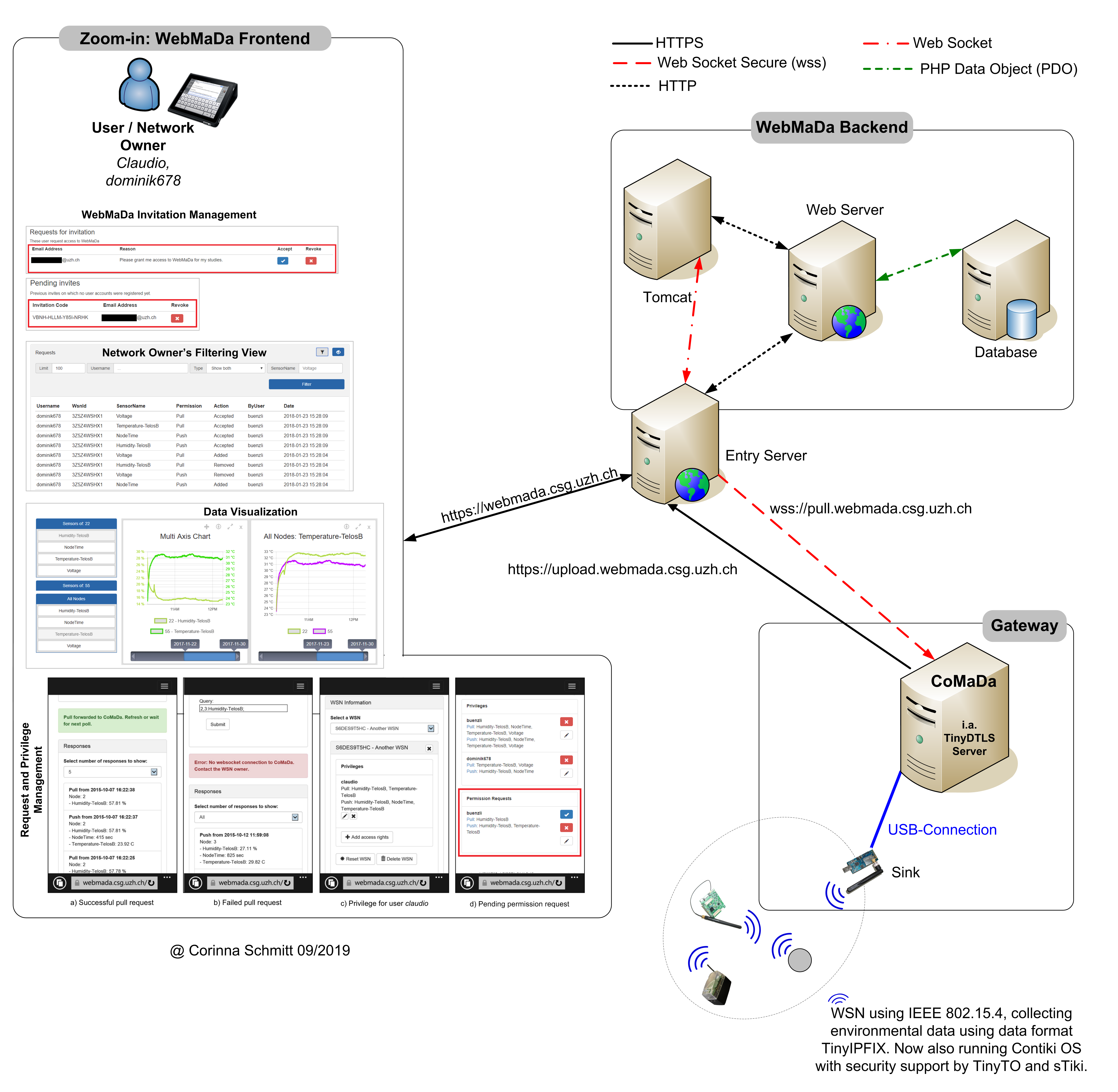
In order to prove that such assumptions and expectations can be fulfilled, a SmartHome/ SmartBuilding scenario is selected for the practical part of this habilitation. This scenario represents one of the famous application areas in the IoT and needs to address all aforementioned identified concerns and requests of the users. A constrained network represents the data source where periodically environmental data (e.g., temperature and humidity) is collected, transmitted in a secure manner to a gateway component which publishes the data gathered via a trustworthy service to authorized users. With this setup a trustwor- thy and flexible IoT framework to monitor environmental data with constrained devices is established, called SecureWSN (Secure Wireless Sensor Network). As SecureWSN is requested to be trustworthy it is assumed that trust is gained by a combination of privacy, security and transparency support realized in by different parts of SecureWSN's component. It is shown that for SecureWSN can address all identified user concerns including E2E security, privacy and trust support, mobile access, and complete data control by the network/data owner. Further, SecureWSN allows immediate request handling in order to react in time in emergency cases or to update granted privileges to avoid misuse of authorized access. In a first step an analysis of existing components (e.g., data format, security solution for device to device communication, and gateway functionalities) is performed, identifying the extensions and updates needed to address user's concerns and request (e.g., mobility support, heterogeneity support of devices, secure communication, and complete data control). In a second step design decisions are specified leading to requirements that need to be met by SecureWSN and a list of tasks that need to be modulated, implemented and integrated. Third, the tasks are addressed and realized having all constrains and assumptions in mind. Finally, each is evaluated to prove that SecureWSN faces all identified challenges and requests establishing a trustworthy and flexible IoT framework for constrained networks monitoring environmental data.
Reference: C.Schmitt:Trust & Security in IoT: Monitoring with Constrained Devices. Habilitation, University of Zurich, Zurich, Switzerland, September 2019.
Dissertation: Secure Data Transmission in Wireless Sensor Networks
Technische Universität München (Germany), Computer Science Department, Chair Network Architectures and Services
Advisor: Prof. Dr.-Ing Georg Carle
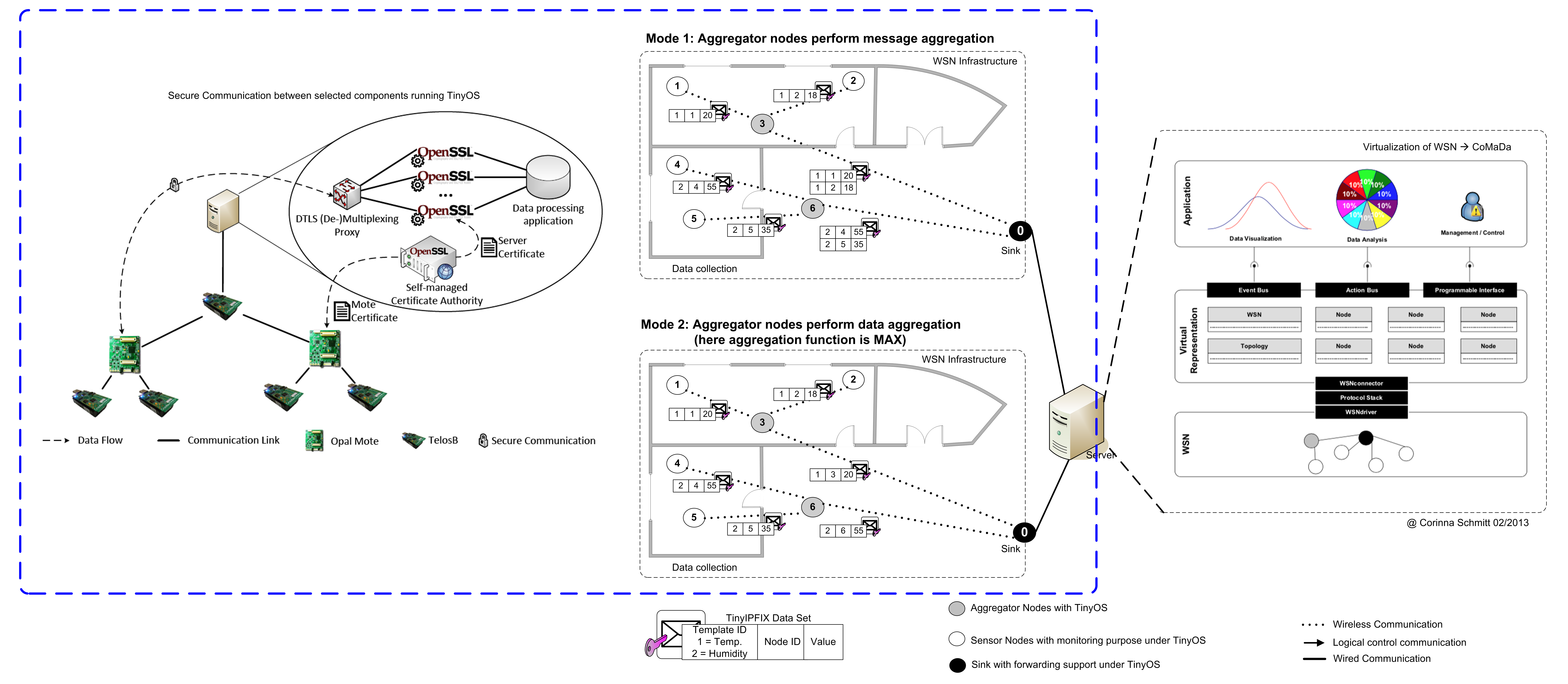
Today a growing number of applications, in particular in the area of cyber-physical systems, depend on data collected by wireless sensor networks. The individual nodes of these networks have severe resource limitations, concerning storage, processing, and transmission capabilities, but also concerning energy available for communication functions. Supporting the required protocol functionality in combination with the goal of energy-saving operation typically results in the development of proprietary, highly specialized communication protocols for wireless sensor networks. However, with Internet technology as the dominating communication paradigm for a wide range of application areas, it became an attractive goal to be able to use Internet protocols within wireless sensor networks. An important functionality within wireless sensor networks is data gathering and aggregation. An Internet protocol standardized within IETF that supports such functionality is the IP Flow Information Export (IPFIX) protocol. In this thesis, concepts for adapting the IPFIX protocol to the needs of wireless sensor networks have been investigated, resulting in the development of the transmission protocol TinyIPFIX, which is an adaptation of the IP Flow Information Export (IPFIX) protocol. The new protocol has been assessed in a representative use case involving a building application. TinyIPFIX has been extended by compression capabilities and by aggregation functionality. Furthermore, extensions to support secure data transmission have been developed, using the protocol Datagram Transport Layer Security (DTLS). This solution ensures that data collected by sensor nodes is transmitted via secure channels to a global data sink, and that authorised access is ensured from a data sink to a wireless sensor network. For validation, a system has been realized that allows configuration of the networks components dynamically, and that supports visualization of the network and the collected data.
Reference: C.Schmitt: Secure Data Transmission in Wireless Sensor Networks. Dissertation, Series Network Architectures and Services, Chair for Network Architectures and Services, Technische Universität München, ISBN: 3-937201-36-X, ISSN: 1868-2634 (print), ISSN: 1868-2642 (electronic), DOI: 10.2313/NET-2013-07-2, Network Architectures and Services NET 2013-07-2, Series Editor: Georg Carle, Technische Universität München, Germany, July 2013
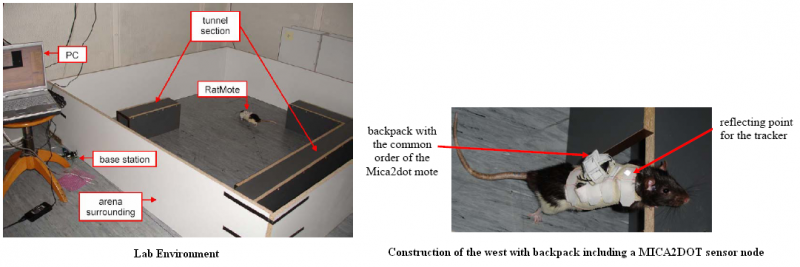
Diploma Thesis: Animal observation using embedded technologies - Rat movement tracking
Eberhard-Karls University of Tübingen (Germany), Computer Science Department - Wilhelm-Schickard-Institut, Chair Network Architectures and Services
Advisors: Prof. Dr.-Ing Georg Carle, Prof. Dr. Hanspeter A. Mallot (Chair of Cognitive Neurobiology), Prof. Dr.-Ing. Klaus Wehrle and M.CS. Olaf Landsiedel (RWTH Aachen)
Today biologists are interested in understanding the general behaviour of animals. They want to analyse the social behaviour of animals and want to observe the moving behaviour. For a humane treatment the studies should be done in the natural environment of the animals without disturbing it. The requirements for field studies are different than in laboratories: The hardware of the used sensor motes must be robust, dimensioned corresponding to the animal, consist of enough memory storage to store as much data as possible, must provide communication possibilities, and get along with limited power resources. All those requirements are provided by embedded systems. In this diploma thesis the technology of the MICA-Family of the Berkeley-Motes are used. They are small and light weighted motes, a radio communication possible, and can also collect sensor readings. The aim of the project is to observe the behaviour of rats corresponding to their meeting behaviour by a static/mobile network. Therefore two algorithms are programmed - Basestation and RatMote. Further more the application side will be programmed to make an analysis of the collected meeting information possible. Finally the functionality is tested in a laboratory.